
Ransomware Attacks Large UK News Site, Demands Bitcoin Payment
A new Cryptesla ransomware is making the rounds throughout the web locking up users files and demanding Bitcoin. Recently the UK news publication The Independent was allegedly compromised by the malicious malware. Trend Micro Blog said that the Cryptesla 2.2.0 had infected the media site by focusing in on its blog page and possibly threatening readers using the WordPress it’s platform. A spokesperson from the Independent tells BBC News:
“IT APPEARS THAT AN ADVERT APPEARING ON THAT BLOG SITE MAY HAVE INCLUDED MALWARE, — THERE IS NO SUGGESTION OR EVIDENCE THAT ANY OF OUR USERS HAVE BEEN AFFECTED BY THIS.” — INDEPENDENT UK SPOKESPERSON
 Ransomware has become an issue for people surfing the web these days and seems to be the new scare from the virus families. According to Trend Micro, a Cryptolocker has infiltrated the WordPress blog hosted by the U.K. publication, Trend Micro says, “The blog page of one of the leading media sites in the United Kingdom, The Independent has been compromised, which may put its reader‘s systems at risk of getting infected with ransomware. We have already informed The Independent about this security incident. However, the site is still currently compromised, and users are still at risk.”
Ransomware has become an issue for people surfing the web these days and seems to be the new scare from the virus families. According to Trend Micro, a Cryptolocker has infiltrated the WordPress blog hosted by the U.K. publication, Trend Micro says, “The blog page of one of the leading media sites in the United Kingdom, The Independent has been compromised, which may put its reader‘s systems at risk of getting infected with ransomware. We have already informed The Independent about this security incident. However, the site is still currently compromised, and users are still at risk.”
This software finds its way into a host computer through an array of vectors and encrypts files, folders and individual areas denying you access to the target regions. Typically users are directed to a ransom note with a timer and asked to pay a sum of bitcoin so the files can be decrypted. There have been many names and types of ransomware including a few variants of the TeslaCrypt version. There haven’t been many successful reports of those paying the ransom demands to the cyber criminals account. However, the ransom note typically gives a 96-hour time frame and says once the ransom is paid a decryption key is given to users so files can be read again. The decryption must take place or users files will always be corrupted and unreadable nonsense.
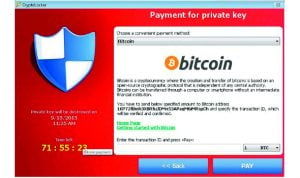 The new 2.2.0 version has said to have been released in October of 2015 according to theTeslaDecoder developer. At the time, the developer says, “Unfortunately unless you capture the encryption key at the time of the infection there is no way of decrypting your files without paying the ransom.” Trend Micro blog says that attacks are part of a systemized campaign against WordPress blogs such as the one provided by the Independent. The latest ransomware encrypts the files by changing names of certain extensions located on your hard drive and asks for $499 in Bitcoin to decrypt the files locked. The particular incident with the Independent blog users were redirected to a new portal that attacked through an Adobe Flash vector claims Trendmicro. The publicationBleeping Computer states:
The new 2.2.0 version has said to have been released in October of 2015 according to theTeslaDecoder developer. At the time, the developer says, “Unfortunately unless you capture the encryption key at the time of the infection there is no way of decrypting your files without paying the ransom.” Trend Micro blog says that attacks are part of a systemized campaign against WordPress blogs such as the one provided by the Independent. The latest ransomware encrypts the files by changing names of certain extensions located on your hard drive and asks for $499 in Bitcoin to decrypt the files locked. The particular incident with the Independent blog users were redirected to a new portal that attacked through an Adobe Flash vector claims Trendmicro. The publicationBleeping Computer states:“UNFORTUNATELY, UNLESS YOU CAPTURE THE ENCRYPTION KEY AT THE TIME OF THE INFECTION THERE IS NO WAY OF DECRYPTING YOUR FILES WITHOUT PAYING THE RANSOM.” — BLEEPING COMPUTER
 The U.S. Federal Bureau of Investigation says that ransomware is on the rise. The attacks are honing in on “home computers,Businesses, financial institutions, government agencies, academic institutions, and other organizations can and have become infected with it as well, resulting in the loss of sensitive or proprietary information, a disruption to regular operations, financial losses incurred to restore systems and files, and/or potential harm to an organization’s reputation” These threats are not just assaulting personal computers and offices but mobile phones as well. In fact the viral attack is ranked the number one mobile threat according to the Blue Coat report. The tech giant IBM has also recognized the ransomware rise in their reports as well. IBM X-Force believes that invasive software like CryptoWall are some of the top threats out there using newer methods regularly.
The U.S. Federal Bureau of Investigation says that ransomware is on the rise. The attacks are honing in on “home computers,Businesses, financial institutions, government agencies, academic institutions, and other organizations can and have become infected with it as well, resulting in the loss of sensitive or proprietary information, a disruption to regular operations, financial losses incurred to restore systems and files, and/or potential harm to an organization’s reputation” These threats are not just assaulting personal computers and offices but mobile phones as well. In fact the viral attack is ranked the number one mobile threat according to the Blue Coat report. The tech giant IBM has also recognized the ransomware rise in their reports as well. IBM X-Force believes that invasive software like CryptoWall are some of the top threats out there using newer methods regularly.
Thankfully quite a few ransomware threats have been decoded by people and organizations throughout the web. People volunteering or also charge a small fee have figured out ways to disable the locking mechanism. Resources can be found at the Kaspersky website, and many other antivirus researchers. It’s recommended that you stay away from untrustworthy domains and odd emails being sent from unknown senders. It’s also suggested to immediately find online help or decryption services that can unlock your files without settling with the demands from a malicious hacker. A bunch of Cryptolocker variants have been cracked so paying a ransom may not be necessary.
What do you think of the rise of ransomware? Let us know in the comments below!
0 Comments
Post a Comment